Recent high-profile incidents have underscored the fact that healthcare cybersecurity threats are escalating. The assault on health systems, hospitals, clinics and their suppliers has catapulted cybersecurity to the top ranks of leadership priorities.
This report aims to enhance leaders’ knowledge as they confront multifaceted, complex challenges. Current data is provided to illuminate cybersecurity status, trends and investment considerations. A number of current best-practice cyber defense recommendations from leading authorities are also explored.
Little Relief in Sight
Healthcare continues to be an attractive target for cyberspace’s bad actors. Personal health information is highly sensitive and therefore valuable. The statistics are sobering, revealing the breadth of attack and the depth of impact.
Range and volume
- Incidents. Over a year recent 6-month period, nearly 8 in 10 organizations experienced one or more security incidents seeking intrusion to IT systems, medical devices and other equipment.[1] footnote [1] Attacks on hospitals rose 120% in 2023 over the previous year.[2] footnote [2] Substantial data breaches have remained persistently high.[3] footnote [3]
- Ransomware. Ransomware has become more prevalent. Over half of surveyed healthcare security professionals said their organizations faced ransomware during the most recent twelve-month period. Forty percent paid the ransom, and 68% experienced patient care disruption.[4] footnote [4] Total industry ransom outlays for 2023 were $1.3 billion.[5] footnote [5]
- Payment Fraud. Another battlefield is fraudulent payment activity. This issue plagues nearly all industries: 80% of business organizations were exposed to actual or attempted payments fraud incidents in 2023, a 15% increase from 2022.[6] footnote [6] Despite progress moving patients and vendors to relatively safer electronic payment rails, use of checks remains substantial. Federal agencies have warned about “a nationwide surge in check fraud schemes targeting the U.S. Mail.”[7] footnote [7] In a multi-industry study, 65% of respondents reported that checks are the method most susceptible to fraud.[8] footnote [8]
- Privacy. Maintaining privacy of patient data is another element in the overall security matrix. Some health systems have incurred multi-million-dollar fines to settle allegations that their websites used third-party tracking software without obtaining consent. A recently published analysis found the issue persists, concluding that “a substantial number of hospital websites did not present users with adequate information about the privacy implications of website use.”[9] footnote [9]
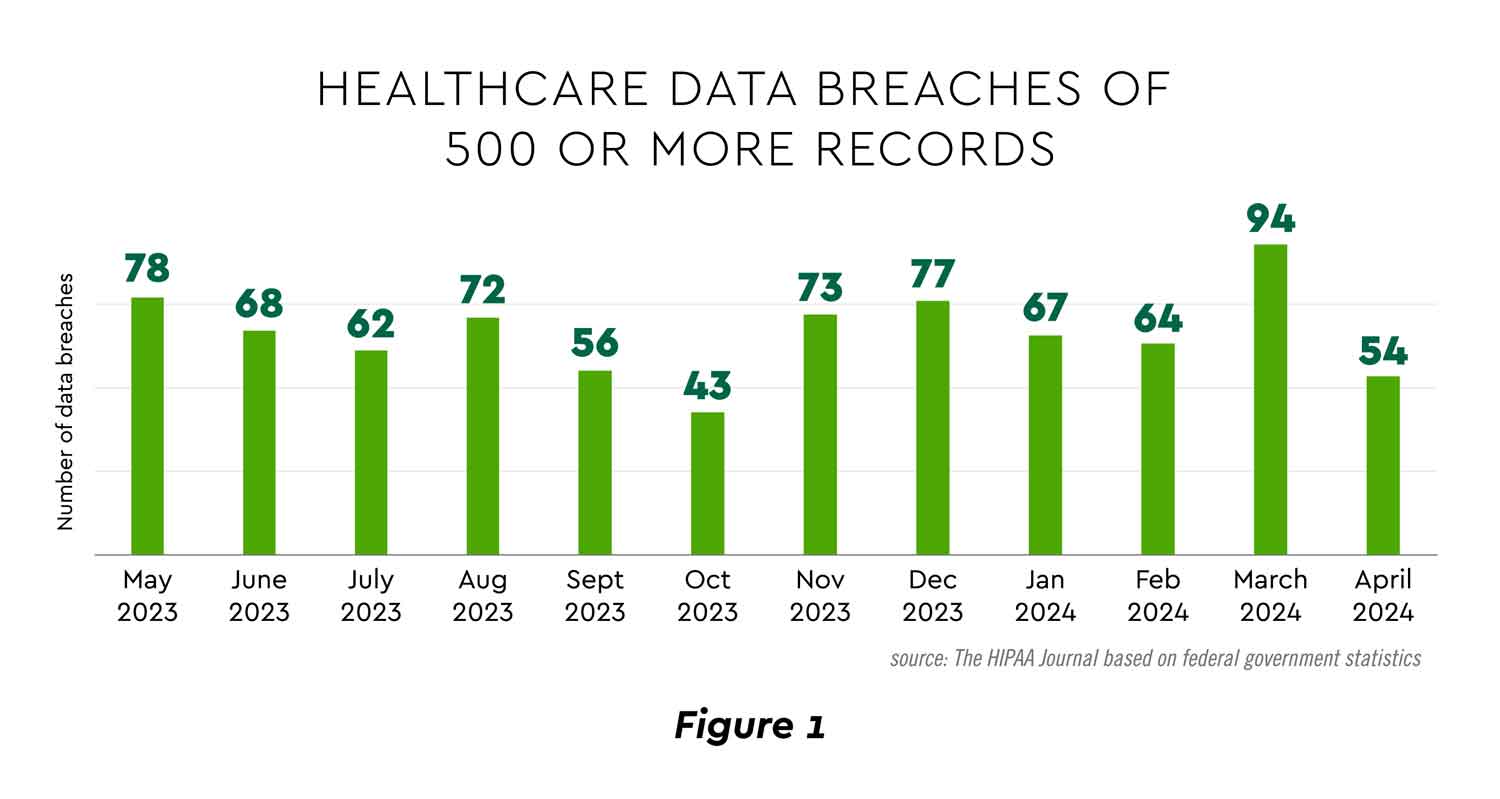
View PDF of Figure 1 PDF opens in a new window[PDF]
Cost and other impacts
Cyber incidents can have many serious and even debilitating consequences that defense and recovery planning must take into account.
- Cost. Hospital and health system data breach costs have increased over 50% in the past three years and reached an average of almost $11 million per incident in 2023.[10] footnote [10] That figure tops other industries. Indirect costs are also rising. Moody’s reports that insurers are reacting to higher claims and weaker profitability by raising hospital cyber insurance premiums and tightening terms and conditions.[11] footnote [11]
- Legal Liability. Significant legal exposure can flow from cybersecurity incidents. As one article succinctly put it, “As cyberattacks against healthcare providers grow in frequency, so too have lawsuits filed by patients aiming to hold systems accountable for alleged damages, including possible violations of privacy.”[12] footnote [12] Two examples reveal the potential magnitude. A New York health system paid almost $5 million to settle a case relating to security lapses that enabled an employee to sell patient data. The recent high-visibility attack on the major Ascension system quickly precipitated two class-action lawsuits claiming negligence by the organization.
- Diminished Trust. Cybersecurity problems can erode the trust patients and staff place in healthcare institutions to the detriment of care, employee engagement and community reputation. The importance of avoiding this erosion is underscored by the high trustworthiness healthcare enjoys among consumers relative to other industries (Figure 2).[13] footnote [13]
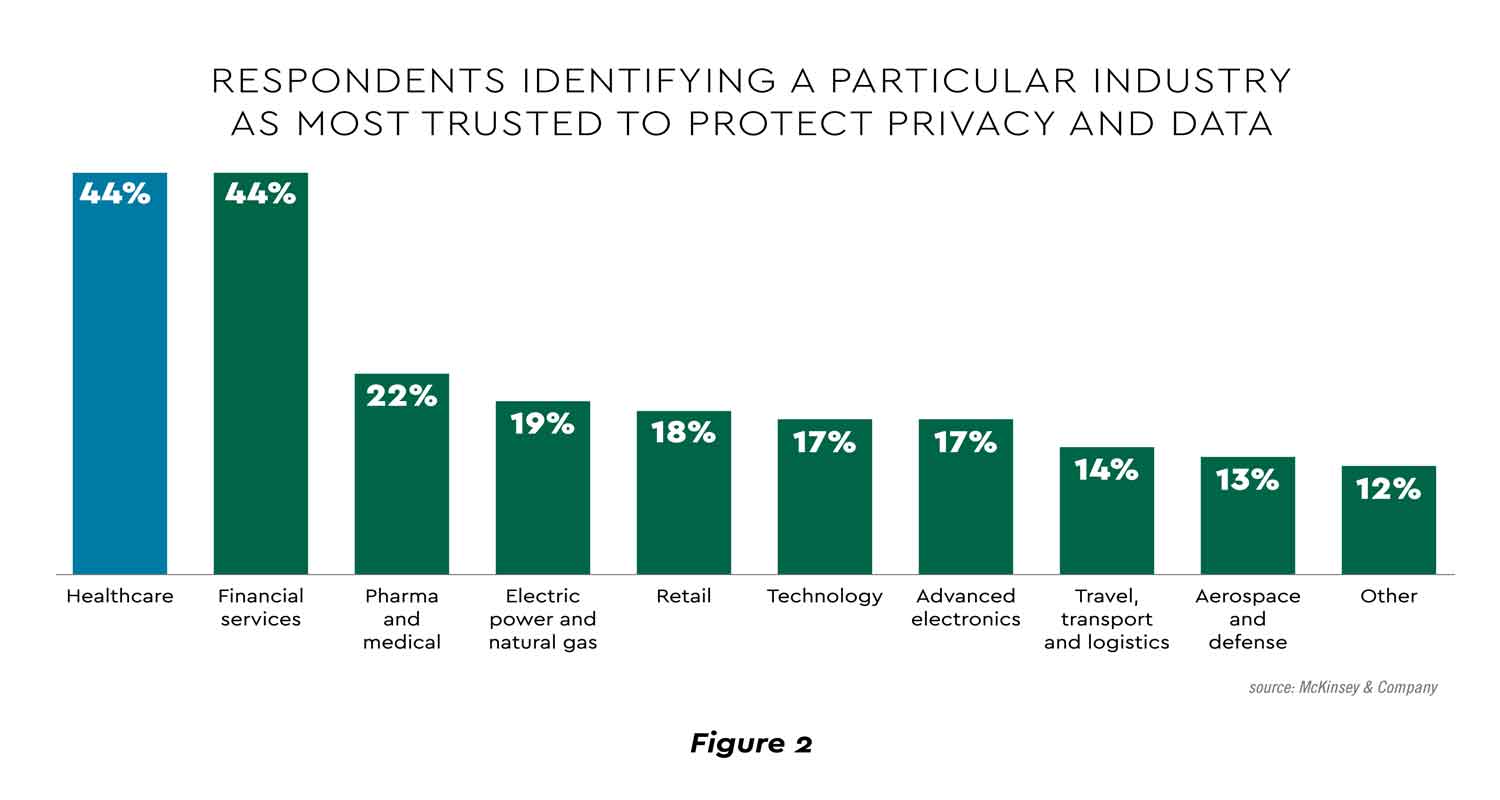
View PDF of Figure 2PDF opens in a new window[PDF]
Cybersecurity and Overall Technology Strategy
Cybersecurity has become a major factor in healthcare technology strategy and investment. A recent poll showed cybersecurity as a leading priority among an important array of digital transformation efforts (Figure 3).[14] footnote [14]
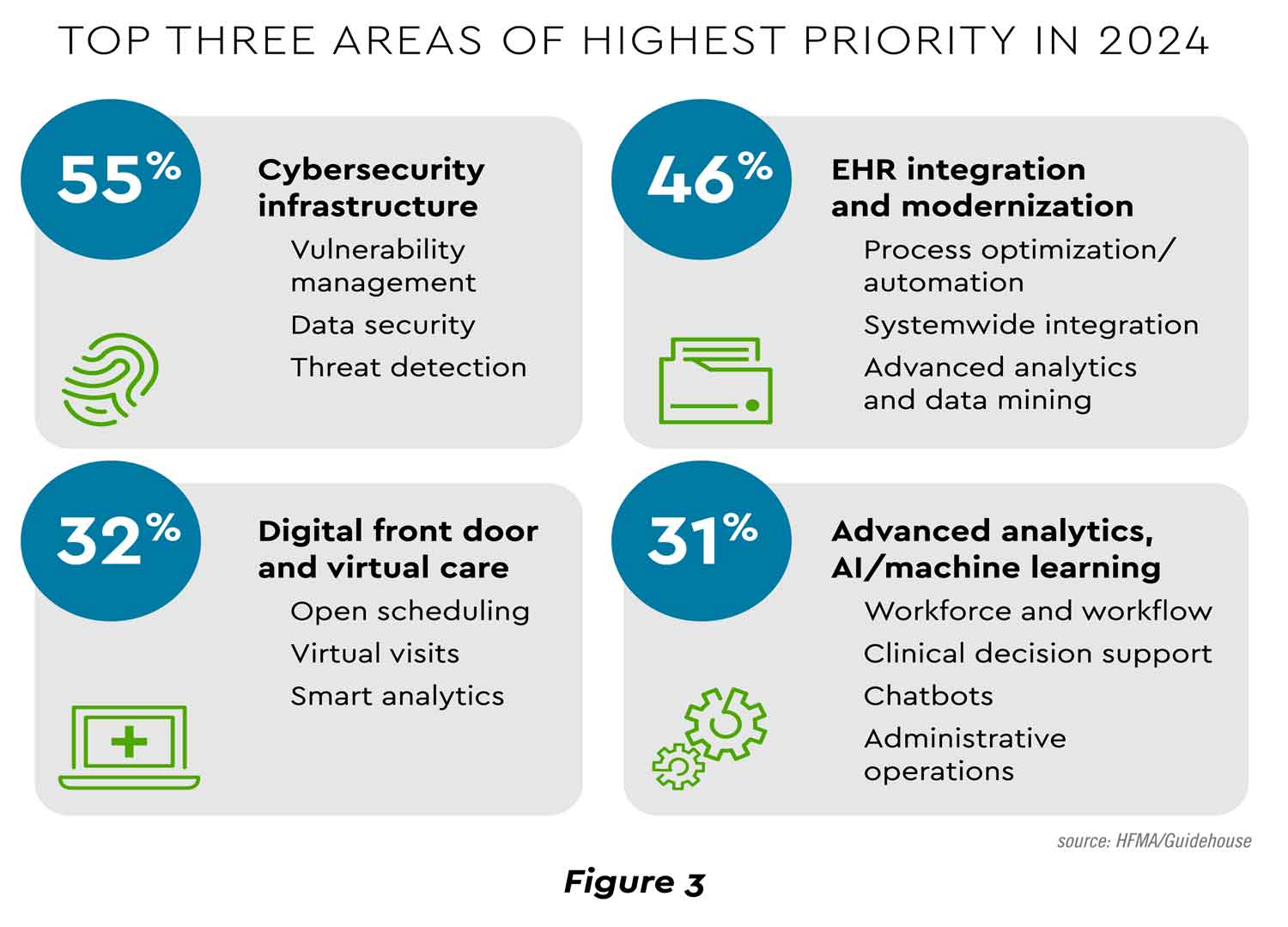
View PDF of Figure 3 PDF opens in a new window[PDF]
Spending on healthcare cybersecurity is projected to increase at over 16% annually to reach $57 billion by 2030.[15] footnote [15] The driver for this growth is a consensus realization that healthcare must reverse its lagging investment. The industry devotes 8.1% of total IT budgets to cybersecurity, second-to-last among studied industries.[16] footnote [16]
Cybersecurity Trends: A Fast-Moving Target
Leaders can feel like they are in a perfect storm regarding the cybersecurity situation. Threats are both fast-changing and expanding at a rapid clip. It is helpful to analyze this shifting landscape along three dimensions.
Surface
What experts call the “attack surface” is steadily broadening, creating more threat opportunities. Gartner enumerates the causes of surface expansion as “accelerated adoption of SaaS, expanding digital supply chains, increased corporate presence on social media, custom application development, remote working and internet-based customer interaction.”[17] footnote [17] One survey documented agreement among 53% of security executives that “there is no such thing as a secure perimeter in today’s digital ecosystem.”[18] footnote [18]
Business email and cloud-based compromise are frequently cited as leading vulnerabilities. Even these well-worn avenues are seeing sophisticated new variations. One is “authentication-in-the- middle,” a process described in this fashion:
- User lured to a phishing site mimicking one normally visited (bank, email, etc.).
- User login captured by attackers and then redirected to the actual site, without the user knowing.
- User enters multifactor authentication code, which is again captured by attackers, allowing them to login to the site.[19] footnote [19]
Mobile devices have created additional vulnerabilities. Across industries, “61% of enterprises still suffer significant losses to mobile fraud, with smishing (SMS phishing) and vishing (voice phishing) being the most prevalent and costly.”[20] footnote [120] Artificial intelligence (AI) is being used to make these techniques more difficult to detect. Unfortunately, 75% of firms have yet to invest in protection against mobile voice and text fraud, a number that likely includes many providers.[21] footnote [21]
One report underscores the expanding attack surface by emphasizing the “Extended Internet of Things (XIoT).” This umbrella term calls attention to the many internet-connected devices today, including elevators, environmental systems, and other operational functions.[22] footnote [22]
Speed
The speed of attack is likewise accelerating. A survey by a leading cybersecurity technology firm revealed that the average “breakout time” — the span from hacker intrusion to lateral movement within the system — was only 62 minutes in 2023, and the fastest recorded incident was just two minutes.[23] footnote [23] Payment fraud is abetted by the increasing velocity with which money can be moved today.
The right detection and response tools must be in place and rapidly deployable. The entire organization is being challenged to maintain maximum agility as these breakout times shrink.
Scope
Healthcare relies on a complex set of suppliers, intermediaries, payers, and other agents, particularly in finance and revenue cycle management. That means the scope of connected entities that may experience a cyber attack that impacts the organization is ever-widening. Gauging risk across this array of firms is difficult.
A further complication is that threats are truly global in origin. A health system CEO observed that breaches are coming from “sophisticated international cyber criminals.”[24] footnote [24] An advisor to the American Hospital Association stated that nearly all attacks on hospitals “originate from criminal gangs based in non-cooperative foreign jurisdictions” such as Russia.[25] footnote [25]
Cybersecurity Strategies
Effective risk management and cyber response require leaders to travel along multiple paths. Cybersecurity strategy and tactics span financial, technological, procedural and cultural categories. A variety of solutions are being pursued in each area.
Stepped up investment
As noted previously, healthcare cybersecurity spending needs to catch up to that of other industries. However, financial pressures are a constraint for many organizations on significant new investment.
What is the right funding level? Each provider will need to make an individual determination, but existing health system spending may offer benchmarks. The average hospital budget for cybersecurity is .37% of revenue, according to a detailed study, with upper quartile larger health system outlays ranging from .42% to .75% of revenue.[26] footnote [26] A related investment consideration is staffing. The median cybersecurity staff count at hospitals is 38 full time equivalents (FTEs).[27] footnote [27] Ranges for upper quartile organizations stand at:
- 101 to 148 FTEs for larger hospitals
- 43 to 80 FTEs for medium-sized hospitals
Matching or exceeding the higher levels will prove challenging for those with limited resources. For some, especially many rural hospitals, outsourcing may be a cost-effective approach. Momentum is growing for this option. One study revealed “a 50% increase in the number of outsourced cybersecurity employees from 2019 to 2022, with for-profit hospitals increasing their outsourced or contract employees 67% and nonprofit hospitals bringing on 11% more outsourced or contracted cybersecurity employees.”[28] footnote [28]
Some believe that the challenge is so great that the government must help. A just-announced initiative represents a step in this direction. A federal agency is investing $50 million to develop a platform capable of probing digital twin models of hospital environments and responding to perceived vulnerabilities with automatic generation, testing and deployment of a fix.[29] footnote [29]
Technology and process solutions
Investment is flowing to a portfolio of established and emerging cybersecurity solutions. Those gaining noteworthy traction and innovation include:
- Core software and processes. Essential security infrastructure continues to rely on evergreen tools such as password management software and passkeys, strong firewalls, multifactor authentication (MFA), aggressive remedial software patches, and endpoint device protection. Though omnipresent, these programs can be compromised by inconsistent usage patterns. For instance, 90% of surveyed organizations use MFA, but admit it suffers from variable deployment “across key systems and critical entry points, creating additional risk of exploitation.”[30] footnote [30]
- Threat intelligence platforms. Data analysis is indispensable to ongoing monitoring of the sources and methods of security threats. By incorporating machine learning and other advanced technologies, threat intelligence platforms process structured and unstructured data at scale to provide insights on threat patterns and are increasingly generating predictions.
- Network segmentation. Dividing one large hospital network into several smaller ones can enhance security through tighter control of user traffic. This strategy represents “a massive and difficult project that can span many years” but one that promises to “accomplish the greatest amount of risk reduction in a healthcare environment and be a pillar in a proactive risk reduction strategy.”[31] footnote [31]
- Zero trust architecture. Harnessing a variety of technologies and operational procedures, zero trust is a comprehensive model with several core tenets: “All data sources are considered resources, all communication is secured regardless of network location, and access to individual organizational resources is granted on a per-session basis.”[32] footnote [32] The vigilance required by this model can be operationally taxing, and observers have warned that clinicians may resist the tight security protocols as another impediment to their efficiency.
- Risk adaptive protection. Productivity is part of the motivation behind another technological approach. Adaptive protection dynamically assigns data controls and policies to individuals based on machine learning risk models so that the most stringent restrictions are “applied only to high-risk users while low-risk users maintain productivity.”[33] footnote [33]
- Payment verification tools. To help mitigate the growing payment fraud discussed earlier, banks such as Commerce Bank offer healthcare organizations the ability to add details to checks and ACH payments that aid in cross-verification prior to payment issuance.
- Artificial intelligence. AI harbors simultaneous potential to proliferate novel security threats as well as enhance defense solutions. As just one example of this duality, AI-generated deepfakes — “highly realistic synthetic media” — are being detected by AI at accuracy rates reaching 90–100%.[34] footnote [34] AI cyber defense is challenged by the need to develop models based on new and unseen threats.[35] footnote [35]
Culture change
People are often the weak link in the security chain. Leaders recognize the need to augment traditional awareness training for employees and users in ways that build a solid, deep-rooted culture of security. Using psychology and analytics principles, a class of security behavior and culture programs (SBCP) is emerging. One consultant delineated seven dimensions of fostering a collective security mindset and rates industries on their maturity of SBCP, with healthcare garnering a “moderate” rating (Figure 4).[36] footnote [36]
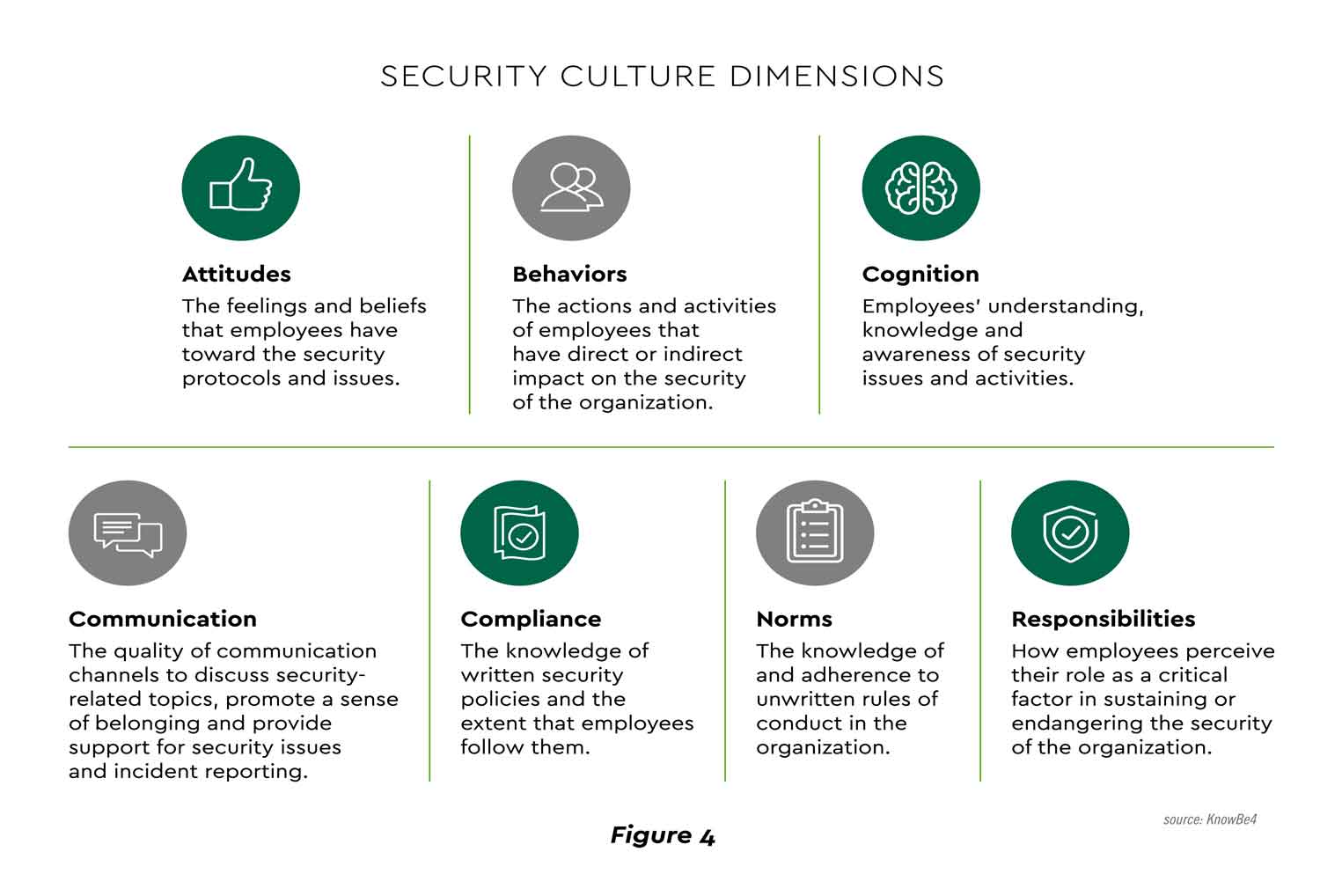
View PDF of Figure 4 PDF opens in a new window[PDF]
Resilience
Many leaders now believe that healthcare providers have overemphasized security to the neglect of resilience, concentrating on “whether they would get attacked instead of on when and how they would respond when it happened.”[37] footnote [37] Resilience aims to minimize the impact of attacks and emerge in a strengthened position. Frequently cited strategies that form the cornerstones of resilience can be grouped into four categories.
Dynamic analysis and learning
Prerequisites for agility and resilience include continually enhancing cybersecurity knowledge and diffusing it throughout the organization. Forward-looking leadership teams are supplementing their internal security tracking with independent cyber audits, advisory input from outside experts and regular employee training.
Streamlining and simplification
The “fog of more” is a phrase coined years ago to denote the seemingly inexorable expansion of cybersecurity defenses being deployed (Figure 5).[38] footnote [38]
View PDF of Figure 5 PDF opens in a new window[PDF]
Clearing some of this fog can pay dividends in security efficiency, effectiveness, and cost. Professionals suggest several ways to consolidate and streamline cybersecurity.
- Designate the organization’s most critical processes. One advisor suggests identifying up to five business processes that are mission critical and mapping the steps of each to “the applications and servers that support them so that teams not only understand priorities for action but can make each critical process more resilient.”[39] footnote [39]
- Simplify the cybersecurity technology stack. Today’s health systems, hospitals and practices generally pursue a “defense-in-depth” strategy designed to reinforce one control layer with others to deter compromise. The resultant collection of security tools can be pruned to create a more focused portfolio that is strategic and calibrated to an organization’s particular needs. This orientation also fits with healthcare’s imperative to “do more with less.”
- Simplify the enterprise technology architecture. Healthcare’s information and medical technology footprint has been characterized by many legacy systems and multiple, often overlapping applications. Developing robust, integrated platforms remains a work in process. A recent study showed that 55% of organizations use over 50 solutions to run healthcare operations.[40] footnote [40] Streamlining this architecture can reduce the threat surface and ease cybersecurity management.
Leadership mindset
Since the cyber resilience project starts with the assumption that attacks and incidents are inevitable, many senior healthcare executives have adopted “a mindset of constant underpreparedness to encourage their teams to continually test and evolve the organization’s ability to respond to an attack.”[41] footnote [41] This discipline appears well-suited to a fast-changing cybersecurity environment.
Measurement
Measuring cybersecurity efforts clarifies readiness status and provides data to evaluate return on investment. Gartner urges tracking of “outcome-driven metrics” against “protection level benchmarks” to help CFOs “make informed cybersecurity investments that balance the need to protect and run their business.”[42] footnote [42] For example, data can be generated to help analyze the value of accelerating software patching from the organization’s current actual performance. The research firm has identified sixteen key measures (Figure 6).
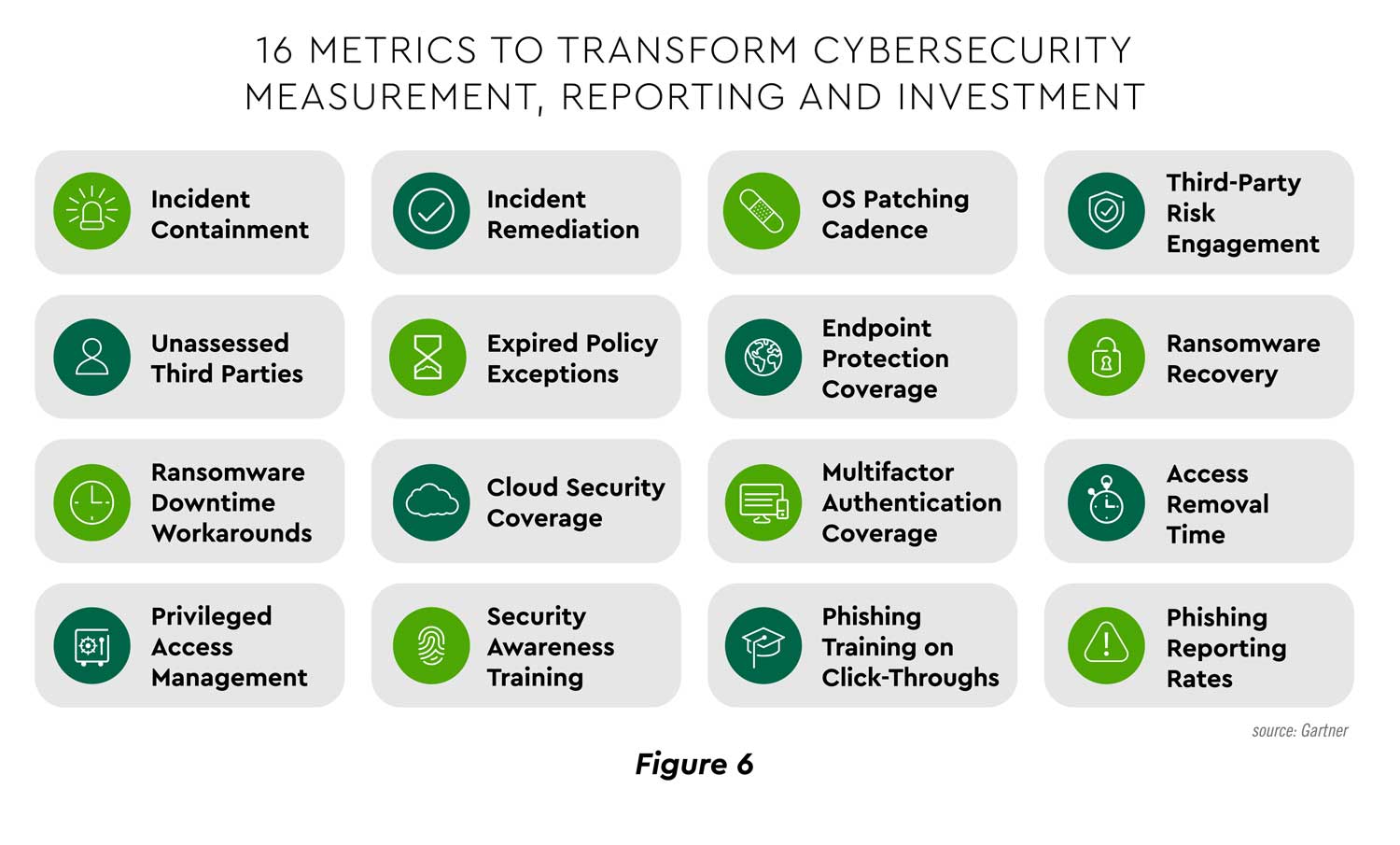
View PDF of Figure 6 PDF opens in a new window[PDF]
As shown earlier in Figure 2, healthcare ranks as the industry consumers trust most to protect data and privacy. Unfortunately, accounts payable and accounts receivable departments are some of the most vulnerable areas of fraud for any industry. This is why Commerce offers several risk management and fraud mitigation solutions so that you can choose the one that’s right for your business. Our tools reduce human errors or interventions, detect suspicious activity and help identify reconciliation discrepancies.
Conclusion
Healthcare cybersecurity is not getting any easier. Organizations are doing what they can, but professionals see a clear need — not just to increase efforts, but also to optimize the solution set through streamlining, focus and more integrated platforms. Advanced technology offers great promise to automate threat detection and response. However, before layering in sophisticated tools and technology, companies need to focus on foundational practices such as timely patch management, strong access control policies, and regular vulnerability assessments. These essentials are the building blocks of a resilient defense framework. Most of all, leaders and experts alike are coalescing around the idea that developing organizational resilience is paramount. Assuming the worst can lead to preparing the best.
These Strategies assume that your organization has a commercially-reasonable base security infrastructure in place. Furthermore, these Strategies should not be your organization’s sole means of protection against fraud losses, but rather they should be included as part of a more comprehensive program implemented by your organization to identify, mitigate, and insure against potential risk from fraud losses. Even if compiled in its entirety, these Strategies do not guaranty against becoming a victim of fraud. This is only an attempt to provide some commonly-accepted practices that may help reduce the likelihood that you become the victim of fraud. Commerce Bank, which is not holding itself out as a security consultant or expert, makes no guaranty, warranty or representation of any kind as to the results that you may achieve by following these Strategies and disclaims any liability related thereto. The term Strategies does not mean or imply that these practices are a definitive or uniformly-accepted compilation of optimal security practices. Check with your cybersecurity consultancy for appropriate actions for your environment.
CommerceHealthcare® solutions are provided by Commerce Bank.
Disclosures:
[1]J. Lagasse, “Almost 80% of Healthcare Organizations Experienced Cyber Incidents in the Past Year,” Healthcare Finance, August 30, 2023.
[2]S. Vogel, “Cybersecurity Takes Center Stage at AHA Annual Meeting,” Healthcare Dive, April 16, 2024.
[3]S. Alder, “April 2024 Healthcare Data Breach Report,” HIPAA Journal, May 20, 2024.
[4]D. Raths, “Survey: Ransomware Attacks Increase, But Cloud Compromise More Concerning,” Healthcare Innovation, October 11, 2023.
[5]S. Vogel, “Cybersecurity Takes Center Stage at AHA Annual Meeting,” Healthcare Dive, April 16, 2024.
[6]Association for Financial Professionals, 2024 Payments Fraud and Control Survey Report, April 2024.
[7]U.S. Department of Treasury Financial Crimes Enforcement Network, “FinCEN Alert on Nationwide Surge in Mail Theft-Related Check Fraud Schemes Targeting the U.S. Mail,” February 27, 2023.
[8]Association for Financial Professionals, 2024 Payments Fraud and Control Survey Report, April 2024.
[9]M.McCoy, A. Wu, S.Burdyl, Y. Kim, et.al., “User Information Sharing and Hospital Website Privacy Policies,” JAMA Network Open, April 11, 2024.
[10]IBM, Cost of a Data Breach Report, July 2023.
[11]A. Condon, “Hospitals Must Boost Cybersecurity Investment Despite Other Costs Weighing on Margins: Moody’s,” Becker’s Hospital CFO Report, April 17, 2023.
[12]S. Vogel, “Ascension Hit with Lawsuits Days After Ransomware Attack.” Healthcare Dive, May 16, 2024.
[13]McKinsey & Company, “Consumers Rule: Driving Healthcare Growth with a Consumer-Led Strategy,” April 2024.
[14]Healthcare Finance Management Association and Guidehouse, 2024 Health System Digital & IT Investment Trends Report, November 2023.
[15]Allied Market Research, Healthcare Cyber Security Market, March 2022.
[16]B. Turner, “Is Cybersecurity Spending Too Low to Prevent Another Change Breach?” Modern Healthcare, April 2024.
[17]Gartner, “Infographic: Top 9 Trends in Cybersecurity for 2024,” 2024.
[18]EY, 2023 Global Cybersecurity Leadership Insights Study, October 2023.
[19]Malwarebytes, “Scammers can Easily Phish Your Multi-Factor Authentication Codes. Here’s How to Avoid It,” May 16, 2024.
[20]Help Net Security, “Vishing, Smishing, and Phishing Attacks Skyrocket 1,265% Post-ChatGPT,” February 29, 2024.
[21]Ibid.
[22]J. Lagasse, “Almost 80% of Healthcare Organizations Experienced Cyber Incidents in the Past Year,” Healthcare Finance, August 30, 2023.
[23]CrowdStrike, 2024 Global Threat Report, February 2024.
[24]C. Van Gorder, “Four Ways Forward in the Aftermath of the Change Healthcare Attack,” Health Leaders, April 2, 2024.
[25]S. Vogel, “Cybersecurity Takes Center Stage at AHA Annual Meeting,” Healthcare Dive, April 16, 2024.
[26]Healthcare and Public Health Sector Coordinating Council, Centers for Medicare and Medicaid Services, and U.S. Department of Health and Human Services, Hospital Cyber Resiliency Initiative Landscape Analysis, April 17, 2023.
[27]Ibid.
[28]L. Dyrda, “Hospitals Bulk Up Cybersecurity Teams, Budgets,” Becker’s Hospital Review, April 25, 2024.
[29]Advanced Research Projects Agency for Health, “ARPA-H Announces Program to Enhance and Automate Cybersecurity for Health Care Facilities,” May 20, 2024.
[30]Healthcare and Public Health Sector Coordinating Council, Centers for Medicare and Medicaid Services, and U.S. Department of Health and Human Services, Hospital Cyber Resiliency Initiative Landscape Analysis, April 17, 2023.
[31]M. Waqas, “Guarding Healthcare’s Digital Frontiers: Predicting 2024’s Cyber Challenges,” Health Data Management, December 12, 2023.
[32]J. McKeon, “Exploring Zero Trust Security in Healthcare, How It Protects Health Data,” HealthIT Security, October 22, 2021.
[33]Microsoft, “Help Dynamically Mitigate Risks with Adaptive Protection,” May 13, 2024.
[34]Booz Allen Hamilton, “Deepfakes Pose Businesses Risks – Here’s What to Know.”
[35]Ibid.
[36]KnowBe4, Security Culture Report 2024, March 26, 2024.
[37]M. Hepfer, R. Chatterjee, and M. Smets, “The CEO’s Cyber Resilience Playbook,” MIT Sloan Management Review, May 1, 2024.
[38]Council on Cybersecurity, Cybersecurity Workforce Handbook, October 2014.
[39]M. Hepfer, R. Chatterjee, and M. Smets, “The CEO’s Cyber Resilience Playbook,” MIT Sloan Management Review, May 1, 2024.
[40]Symplr, 2023 Symplr Compass Report, October 2023.
[41]M. Hepfer, R. Chatterjee, and M. Smets, “The CEO’s Cyber Resilience Playbook,” MIT Sloan Management Review, May 1, 2024.
[42]Gartner, “Gartner Says CFOs Must Treat Cybersecurity as a Business Decision,” May 21, 2024.
